- User ID
- 1
- Joined
- 7 Jan 2019
- Messages
- 1,142
- Reaction score
- 58
- Points
- 48
This is an updated tutorial from my previous RouterOS v6.43 L2TP/IPsec tutorial.
In RouterOS v6.44 there were major changes where they removed "main-l2tp" exchange-mode from the /ip ipsec peer.
But this means configuring L2TP/IPsec is even more simpler, just follow through my guide down below:

If you have any questions or comments, feel free to post down below
In RouterOS v6.44 there were major changes where they removed "main-l2tp" exchange-mode from the /ip ipsec peer.
But this means configuring L2TP/IPsec is even more simpler, just follow through my guide down below:
- Create the L2TP Server
The commands below will:- Enable the L2TP Server;
- Enable IPsec over L2TP;
- Set your desired IPsec PSK.
-
Rich (BB code):
/interface l2tp-server server set enabled=yes set use-ipsec=required set ipsec-secret=<yourIPsecPSKhere> - MikroTik will create IPsec Policies
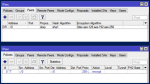
On the IPsec Peers tab, we can see the Dynamic IPsec Peer (Phase 1) has been active;
As well as on the IPsec Policies tab, we can see the Dynamic IPsec Policy (Phase 2) has been active. - Create a VPN Address Pool for the Client Devices
The commands below will:- Add the start & end addresses to hand out for the L2TP sessions;
- Note: These IP addresses can be any address range and I would recommend that they do not match existing IP address in the MikroTik.
-
Rich (BB code):
/ip pool add name=pool1-L2TP_users ranges=10.0.7.2-10.0.7.14 - Create a VPN User Profile to apply to L2TP clients
Notes:- Local Address acts as Default Gateway for the L2TP Client.
- Routers LAN IP Address
- Pool Address Static Entry
- Dynamic Selection from the Pool itself
- Local Address acts as Default Gateway for the L2TP Client.
-
Still on this PPP Profile window:Rich (BB code):
/ppp profile add name=profile1-L2TP_users local-address=10.0.7.1 remote-address=pool1-L2TP_users- If you go to the Protocols tab, you can adjust any protocols to suit.
- On the Limits tab, you can set session timers & rate limits for clients, set timeout - maximum connection time, idle timeout - link termination after no activity, rate limit connection speeds, only one - can user have more than 1 connection or not.
- Scripts on up and down, and many more.
- User Login Credentials
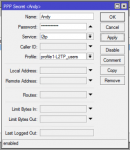
Notes:- Name & Password are the login details.
- Select L2TP as the Service
- Profile to use for this users login.
-
Rich (BB code):
/ppp secret add name=Andy password=<yourVPNpassword> service=l2tp profile=profile1-L2TP_users - Optionally: Check Firewall Rules
Rich (BB code):/ip firewall filter add chain=input protocol=udp dst-port=500,1701,4500 in-interface=ether1-GTW - Our L2TP over IPsec Policy is now complete
If you have any questions or comments, feel free to post down below