You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
MikroTik Site-to-Site IPsec Tunnel
- Thread starter Andy
- Start date
Both PFS is set to none.
I think it's a firewall issue, I forgot to allow ESP traffic, and when I set things up the first time, I did some pings and that establishes the connection. But after the lifetime of connections finishes, it needs to reestablish and somehow could not establish by itself.
Allowing ESP traffic in the firewall seems to fix the issue. It's been running for a while now.
I think it's a firewall issue, I forgot to allow ESP traffic, and when I set things up the first time, I did some pings and that establishes the connection. But after the lifetime of connections finishes, it needs to reestablish and somehow could not establish by itself.
Allowing ESP traffic in the firewall seems to fix the issue. It's been running for a while now.
Hi,
If I have multiple wan (ex. wan1 and wa2) and I want to make a backup IPSec tunnel, so If wan1 goes down I can use wan2, how can I do?
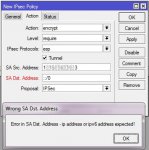
I've linked subnet 192.168.100.0/24 to 192.168.178.0/24 and vicevera through an IPSec tunnel and SA Src. Address in wan1 (ex 1.1.1.1) an it works; but if I want to link the same subnets using SA Src. Address in wan2 (ex 2.2.2.2) and the same SA Dst. Address I got an error inside mikrotik GUI:
So is there a way to have 2 IPSec tunnel that are connecting the same subnets?
Can I maybe use templates for this? But I don't understand how to use them, I didn't find mach docs about this.
Before use pure IPSec I was used to create some IP-IP tunnels before and over these tunnels I configured IPSec; in this way I got routed tunnels with different priorities and so If one failed I was able to use the second that was always on but with less priority.
Is there a way to have this same behavior with pure IPSec?
Thanks.
If I have multiple wan (ex. wan1 and wa2) and I want to make a backup IPSec tunnel, so If wan1 goes down I can use wan2, how can I do?
I've linked subnet 192.168.100.0/24 to 192.168.178.0/24 and vicevera through an IPSec tunnel and SA Src. Address in wan1 (ex 1.1.1.1) an it works; but if I want to link the same subnets using SA Src. Address in wan2 (ex 2.2.2.2) and the same SA Dst. Address I got an error inside mikrotik GUI:
So is there a way to have 2 IPSec tunnel that are connecting the same subnets?
Can I maybe use templates for this? But I don't understand how to use them, I didn't find mach docs about this.
Before use pure IPSec I was used to create some IP-IP tunnels before and over these tunnels I configured IPSec; in this way I got routed tunnels with different priorities and so If one failed I was able to use the second that was always on but with less priority.
Is there a way to have this same behavior with pure IPSec?
Thanks.
- User ID
- 1
- Joined
- 7 Jan 2019
- Messages
- 1,536
- Reaction score
- 125
- Points
- 63
Have you defined the other end's LAN network?
Your Winbox layout is a bit different than mine, are you using the latest Winbox version (I'm currently using v3.21-x64)
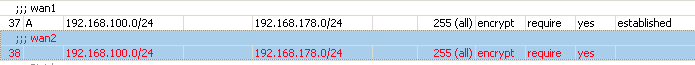
And here's one of my established IPsec -> Policies tab:
View attachment 155View attachment 156View attachment 157
On the IPsec -> Peers tab, you can fill with ::/0 if you want to accept all IPsec connection regardless their source IP address.
Hi @Andy,
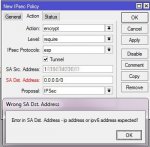
Thanks to your kind work and let us figure out the basic setting guide for IPsec Peer to Peer. First of all I am totally noob about this Mikrotik, The same message appear for SA.dst address when I trying to save the configuration. My Mikrotik now with 6.43.8, the latest is 6.46.6 so mean that we need to upgrade so to overcome this problem? Putting in ::/0 does the same thing same error message appear.
PS: Under my Peer tab and Identities tab all is empty...... Just not sure how to set it too.....
If my setting was incorrect please help to correct me, I am not networking savvy I only know very simple basic thing.
Thanks in advance.
My network setup as shown as the diagram below.
Last edited:
- User ID
- 1
- Joined
- 7 Jan 2019
- Messages
- 1,536
- Reaction score
- 125
- Points
- 63
Hi @Edwink,Hi @Andy,
Thanks to your kind work and let us figure out the basic setting guide for IPsec Peer to Peer. First of all I am totally noob about this Mikrotik, The same message appear for SA.dst address when I trying to save the configuration. My Mikrotik now with 6.43.8, the latest is 6.46.6 so mean that we need to upgrade so to overcome this problem? Putting in ::/0 does the same thing same error message appear.
PS: Under my Peer tab and Identities tab all is empty...... Just not sure how to set it too.....
If my setting was incorrect please help to correct me, I am not networking savvy I only know very simple basic thing.
Thanks in advance.
My network setup as shown as the diagram below.
View attachment 176
View attachment 177
View attachment 178
- SA Src. Address: fill it with your source WAN address.
- SA. Dst. Address: fill it with the other router's WAN address, you can fill it with 0.0.0.0 if the other router has a dynamic WAN address.
Hi @Edwink,
See my screenshot below: (I tested on RouterOS v6.44.5)
- SA Src. Address: fill it with your source WAN address.
- SA. Dst. Address: fill it with the other router's WAN address, you can fill it with 0.0.0.0 if the other router has a dynamic WAN address.
View attachment 179
Hi @Andy
- SA Src. Address: I already fill with source WAN address.
- SA. Dst. Address: is dynamic so I have try fill with 0.0.0.0 and also try with ::/0 and also "empty" but return same error message appear.
Above is our existing networking layout
Both are Mikrotik RB3011 updated to latest ROM 6.46.6
Planning :
1.Moving back "server 3" from "site 2" to "site 1"
2. Site 2 clients will access Server 3 on site 1 by IPsec site2 site VPN
Query:
1. Can we maintain all same range IP subnet 192.168.1.x/24 or create another IP subnet range 192.168.2.0/24 for Server 3? Is it possible to maintain 2 IP range under one router or just maintain same range easy to maintain?
2. Concern about the accounting system speed reluctant due to access through WAN
Total Networking devices:
Server-3
Client-40
Network printer-6
Thanks in advance.
Edwin
- User ID
- 1
- Joined
- 7 Jan 2019
- Messages
- 1,536
- Reaction score
- 125
- Points
- 63
I wouldn't recommend using the same IP network for 2 different sites.1. Can we maintain all same range IP subnet 192.168.1.x/24 or create another IP subnet range 192.168.2.0/24 for Server 3? Is it possible to maintain 2 IP range under one router or just maintain same range easy to maintain?
I'd use something like 192.168.1.0/24 for site 1 and 192.168.2.0/24 for site 2.
With this configuration, it'll be much easier to manage the network in the future, as well as implementing a site-to-site IPsec tunnel.
Site-to-site IPsec tunnel if configured properly shouldn't have any speed degradation over WAN.2. Concern about the accounting system speed reluctant due to access through WAN
This is also depending on your WAN connection, if it's a fibre, there shouldn't be an issue on both upload & download speed.
If it's a DSL line, you'll probably have a slower upload speed.
In NZ, mostly we have 100 Mbps fibres & gigabit fibres, I barely find any issues with both uploading and downloading using site-to-site IPsec, except on rural areas who are still on DSL connections.
I wouldn't recommend using the same IP network for 2 different sites.
I'd use something like 192.168.1.0/24 for site 1 and 192.168.2.0/24 for site 2.
With this configuration, it'll be much easier to manage the network in the future, as well as implementing a site-to-site IPsec tunnel.
Site-to-site IPsec tunnel if configured properly shouldn't have any speed degradation over WAN.
This is also depending on your WAN connection, if it's a fibre, there shouldn't be an issue on both upload & download speed.
If it's a DSL line, you'll probably have a slower upload speed.
In NZ, mostly we have 100 Mbps fibres & gigabit fibres, I barely find any issues with both uploading and downloading using site-to-site IPsec, except on rural areas who are still on DSL connections.
Hi Andy,
Thanks for your suggestion, I will implement all necessary configuration just to make it work way more better.
But until now I still can't pass through the ::/0 or 0.0.0.0 in the "SA Dst address" in Policies Tab, hope you can figure out for me.
Anyway if we reverse it and put in the 0.0.0.0 in "SA src address" and and fix WAN IP actual address in "SA Dst address" than it can apply without any issue.
Attachments
- User ID
- 1
- Joined
- 7 Jan 2019
- Messages
- 1,536
- Reaction score
- 125
- Points
- 63
Hi @Edwink,
All good mate, I look forward to hearing your IPsec tunnel up and running!
Let's try a different approach, go to your IPsec -> Identities, create a new peer identity with port override on the Generate Policy.
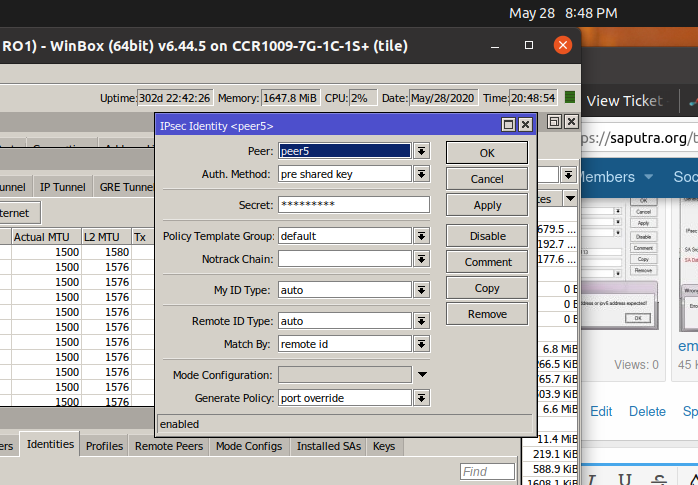
By doing port override, phase 2 will be dynamic, meaning you don't need to set up phase 2, ultimately you will be able to adjust phase 1 as you like.
Hope this works for you.
Cheers
All good mate, I look forward to hearing your IPsec tunnel up and running!
Let's try a different approach, go to your IPsec -> Identities, create a new peer identity with port override on the Generate Policy.
By doing port override, phase 2 will be dynamic, meaning you don't need to set up phase 2, ultimately you will be able to adjust phase 1 as you like.
Hope this works for you.
Cheers