- User ID
- 1
- Joined
- 7 Jan 2019
- Messages
- 1,505
- Reaction score
- 120
- Points
- 63
Follow this easy seven steps, and you'll get your MikroTik IPsec Site-to-Site Tunnel established 
This is the updated version of my original easy guide on how to set up MikroTik Site-to-Site IPsec Tunnel.
Tested on RouterOS v6.45.9 and it's fully working & functional.
If you are working from WAN, don’t forget to enable Safe Mode.
1. IPsec Proposals
Let’s start from Winbox -> IP -> IPsec -> Proposals, and this is the IPsec proposal I normally use:
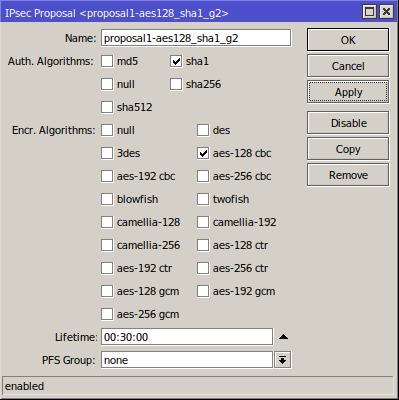
2. IPsec Profiles
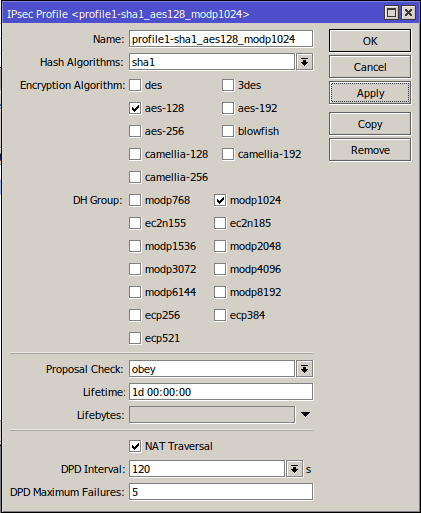
3. IPsec Peers
Here you want to fill the address with the other router's WAN IP address:
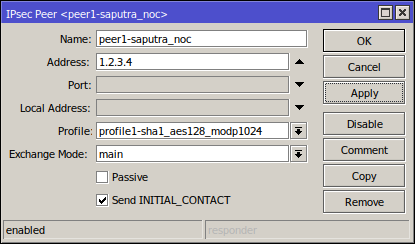
Situational:
If the other router has a dynamic WAN IP address, leave the Address empty, once you click Apply that will be filled with "::/0" and you might get a red warning: --- This entry is unreachable, that warning will go by itself when you do Step 5. Only one router must have this peer configured with a correct WAN IP.
Another Situational:
If the router already has L2TP/IPsec and you want your MikroTik to accept site-to-site IPSec VPN's from dynamic peers then you don't need to do anything. Why? You only need to have 1 Peer configured with ::/0 and they must all use the same pre-shared key (i.e. using PSK from IPsec Secret found in the L2TP/IPsec configuration) as the l2tp-in-server phase 2 has "Port Strict", the phase 2 will establish dynamically.
However, with this configuration, if you have 2 remote sites on the same IP range, the VPN may fail as it will not know where the return traffic is supposed to go.
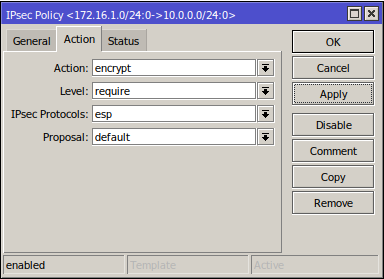
4. IPsec Policies
Here, we fill Src. Address with the current router's LAN IP address, and Dst. Address with the other router's LAN IP address, and make sure that you have Tunnel enabled and leave the Action tab as default:
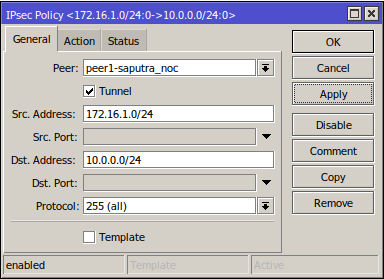
5. IPsec Identities
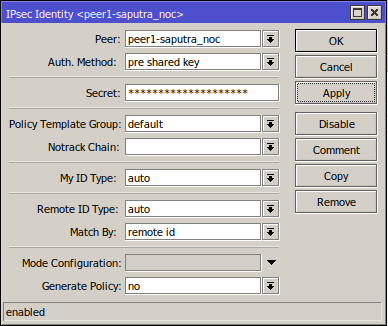
Situational:
If the other router has a dynamic WAN IP address, you can set Generate Policy: to use port strict. (i.e. to use ports from peer's proposal, which should match peer's policy.)
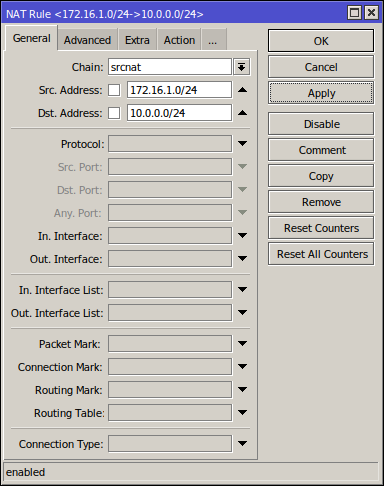
6. Firewall NAT
For the LAN networks to be able to talk with each other, set up the following firewall:
Here, we fill Src. Address with the current router's LAN IP address, and Dst. Address with the other router's LAN IP address and set Action to accept:
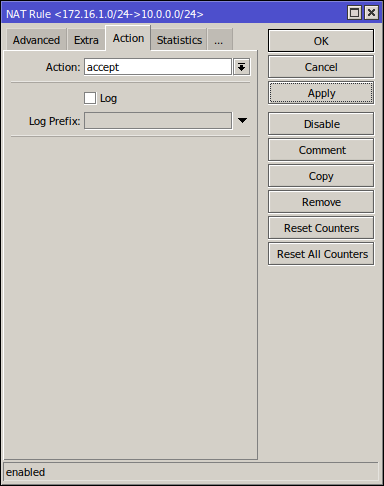
Make sure you put this rule above your main NAT masquerade, otherwise it'll not work.
7. Repeat
Oops, did we forget that we haven't done anything on the other router?
Repeat this task on the other router and you will have your site-to-site tunnel established
FAQ:
Q: Who will be the initiator/responder?
A: In MikroTik normally both side initiator, so whichever router initiates first, the other router will become the responder. Except if you tick Passive on step 3, then the MikroTik will not try and establish the IPsec connection, instead, it waits for incoming connections.
Q: What's Send INITIAL_CONTACT on step 3?
A: It specifies whether to send "initial contact" IKE packet or wait for the remote side, this packet should trigger the removal of old peer SAs for the current source address.
I hope this tutorial been useful to you
If you have any questions, feel free to post them down below
This is the updated version of my original easy guide on how to set up MikroTik Site-to-Site IPsec Tunnel.
Tested on RouterOS v6.45.9 and it's fully working & functional.
If you are working from WAN, don’t forget to enable Safe Mode.
1. IPsec Proposals
Let’s start from Winbox -> IP -> IPsec -> Proposals, and this is the IPsec proposal I normally use:
2. IPsec Profiles
3. IPsec Peers
Here you want to fill the address with the other router's WAN IP address:
Situational:
If the other router has a dynamic WAN IP address, leave the Address empty, once you click Apply that will be filled with "::/0" and you might get a red warning: --- This entry is unreachable, that warning will go by itself when you do Step 5. Only one router must have this peer configured with a correct WAN IP.
Another Situational:
If the router already has L2TP/IPsec and you want your MikroTik to accept site-to-site IPSec VPN's from dynamic peers then you don't need to do anything. Why? You only need to have 1 Peer configured with ::/0 and they must all use the same pre-shared key (i.e. using PSK from IPsec Secret found in the L2TP/IPsec configuration) as the l2tp-in-server phase 2 has "Port Strict", the phase 2 will establish dynamically.
However, with this configuration, if you have 2 remote sites on the same IP range, the VPN may fail as it will not know where the return traffic is supposed to go.
4. IPsec Policies
Here, we fill Src. Address with the current router's LAN IP address, and Dst. Address with the other router's LAN IP address, and make sure that you have Tunnel enabled and leave the Action tab as default:
5. IPsec Identities
Situational:
If the other router has a dynamic WAN IP address, you can set Generate Policy: to use port strict. (i.e. to use ports from peer's proposal, which should match peer's policy.)
6. Firewall NAT
For the LAN networks to be able to talk with each other, set up the following firewall:
Here, we fill Src. Address with the current router's LAN IP address, and Dst. Address with the other router's LAN IP address and set Action to accept:
Make sure you put this rule above your main NAT masquerade, otherwise it'll not work.
7. Repeat
Oops, did we forget that we haven't done anything on the other router?
Repeat this task on the other router and you will have your site-to-site tunnel established
FAQ:
Q: Who will be the initiator/responder?
A: In MikroTik normally both side initiator, so whichever router initiates first, the other router will become the responder. Except if you tick Passive on step 3, then the MikroTik will not try and establish the IPsec connection, instead, it waits for incoming connections.
Q: What's Send INITIAL_CONTACT on step 3?
A: It specifies whether to send "initial contact" IKE packet or wait for the remote side, this packet should trigger the removal of old peer SAs for the current source address.
I hope this tutorial been useful to you
If you have any questions, feel free to post them down below
