- User ID
- 1
- Joined
- 7 Jan 2019
- Messages
- 1,142
- Reaction score
- 58
- Points
- 48
Starting from RouterOS version v6.47 it is possible to use DNS over HTTPS (DoH). DoH uses the HTTPS protocol to send and receive DNS requests for better data integrity. Its main goal is to provide privacy by eliminating man-in-the-middle attacks (MITM). Currently, DoH is not compatible with FWD type static entries, to utilise FWD entries, DoH must not be configured.
DNS hijacking, DNS poisoning, or DNS redirection is the practice of subverting the resolution of Domain Name System (DNS) queries. This problem can be remedied by implementing DNS over HTTPS.
Importing the root CA certificate of the DoH server you have chosen to use for increased security is advised.
There are various ways to find out what root CA certificate is necessary. The easiest way is by using your WEB browser, navigating to the DoH site and checking the website's security. Using Firefox we can see that DigiCert Global Root CA is used by the CloudFlare DoH server. You can download the certificate straight from the browser or navigate to DigiCert website and fetch the certificate from a trusted source.
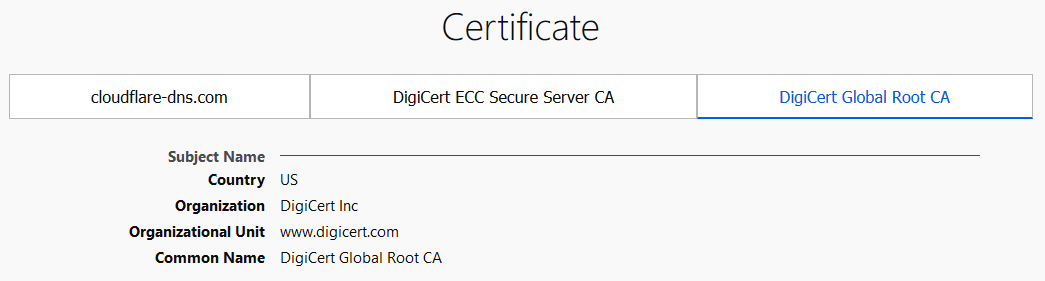
Download the certificate and import it:
Configure the DoH server:
Note that you need at least one regular DNS server configured for the router to resolve the DoH hostname itself. If you do not have any dynamical or static DNS server configured, configure it like this:
Based on MikroTik guide https://wiki.mikrotik.com/wiki/Manual:IP/DNS
You would also need to configure cloudflare-dns.com as a static DNS entry, in order the MikroTik would know where to connect to the DoH Server:
DNS hijacking, DNS poisoning, or DNS redirection is the practice of subverting the resolution of Domain Name System (DNS) queries. This problem can be remedied by implementing DNS over HTTPS.
Importing the root CA certificate of the DoH server you have chosen to use for increased security is advised.
Warning: We strongly suggest to not use third party download links for certificate fetching. Use the Certificate Authority own website.
There are various ways to find out what root CA certificate is necessary. The easiest way is by using your WEB browser, navigating to the DoH site and checking the website's security. Using Firefox we can see that DigiCert Global Root CA is used by the CloudFlare DoH server. You can download the certificate straight from the browser or navigate to DigiCert website and fetch the certificate from a trusted source.
Download the certificate and import it:
Rich (BB code):
/tool fetch url="https://cacerts.digicert.com/DigiCertGlobalRootCA.crt.pem"
/certificate import file-name=DigiCertGlobalRootCA.crt.pem passphrase=""
Rich (BB code):
/ip dns set use-doh-server=https://cloudflare-dns.com/dns-query verify-doh-cert=yes
Rich (BB code):
/ip dns set servers=1.1.1.1Based on MikroTik guide https://wiki.mikrotik.com/wiki/Manual:IP/DNS
You would also need to configure cloudflare-dns.com as a static DNS entry, in order the MikroTik would know where to connect to the DoH Server:
Code:
/ip dns static
add address=2606:4700::6810:f8f9 name=cloudflare-dns.com type=AAAA
add address=2606:4700::6810:f9f9 name=cloudflare-dns.com type=AAAA
add address=104.16.248.249 name=cloudflare-dns.com
add address=104.16.249.249 name=cloudflare-dns.com
Last edited:
