- User ID
- 1
- Joined
- 7 Jan 2019
- Messages
- 1,546
- Reaction score
- 126
- Points
- 63
I don't think it's ideal running a service with TLS 1.1 and 1.0 in 2020.
These ciphers are considered insecure and need to be disabled.
Two things we will be looking at is the use of insecure encrypted protocols and legacy cipher suites that are unfortunately still enabled on Windows Server 2019. If you do heaps of PCI compliance then you should be familiar with the mandate that SSL and TLS 1.0 should no longer be used after 30th of June 2016.
We will disable both TLS 1.1 and 1.0 on Windows Server 2019 through the registry editor in the following location:
Initially, you will most likely find the Protocols key (folder) empty.
We'll create keys called TLS 1.1 and TLS 1.0 and subkeys for both Client and Server. Along with those, we'll create a DWORD (32-bit) Value called Enabled and set the value to 0 as shown in the screenshots below:
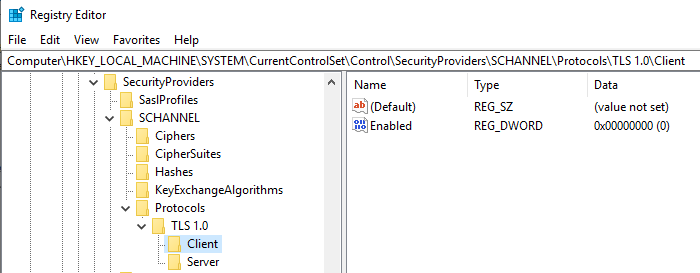
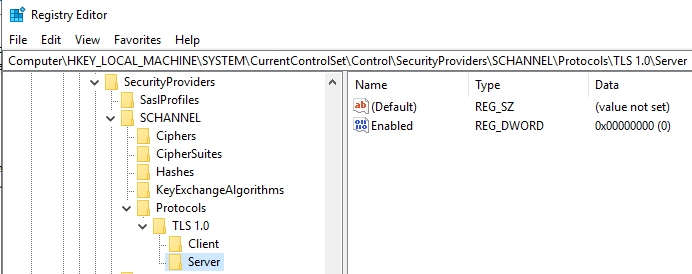
Next, we'll need to establish this cipher suite order in group policy. Open up gpedit.msc and navigate to the following policy:
Insert the cipher suites in the following order in accordance with the referenced Microsoft Documentation:
https://docs.microsoft.com/en-us/windows/desktop/secauthn/tls-cipher-suites-in-windows-10-v1809
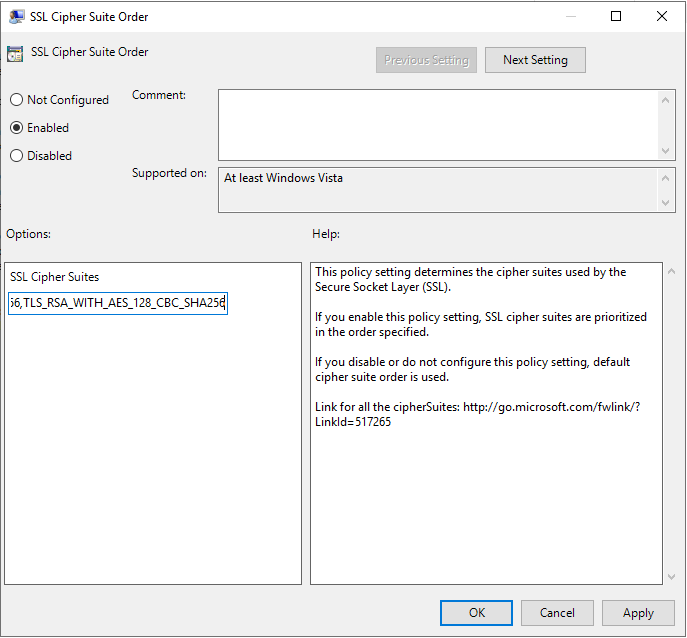
The next step is we're going to reboot the target server, and your web server will no longer negotiate over TLS 1.1 and 1.0 since we've disabled them through the Window Registry.
I used this solution on Windows Server 2019 + IIS 10.0, but I think this solution should work on an earlier version of Windows too
Let me know if you find this solution useful for you by commenting down below 
These ciphers are considered insecure and need to be disabled.
Two things we will be looking at is the use of insecure encrypted protocols and legacy cipher suites that are unfortunately still enabled on Windows Server 2019. If you do heaps of PCI compliance then you should be familiar with the mandate that SSL and TLS 1.0 should no longer be used after 30th of June 2016.
We will disable both TLS 1.1 and 1.0 on Windows Server 2019 through the registry editor in the following location:
Code:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Initially, you will most likely find the Protocols key (folder) empty.
We'll create keys called TLS 1.1 and TLS 1.0 and subkeys for both Client and Server. Along with those, we'll create a DWORD (32-bit) Value called Enabled and set the value to 0 as shown in the screenshots below:
Right-click on the Protocols, and select New -> Key
Type in: TLS 1.1
Right-click on TLS 1.1 key, and again select New -> Key
Type in: Server
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and leave the value to 0x00000000 (0) as we're going to disable it.
If you want to prevent the server from negotiating using TLS 1.1 to other hosts:
Right-click on TLS 1.1 key, and again select New -> Key
Type in: Client
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and leave the value to 0x00000000 (0) as we're going to disable it.
--
And now we're going to disable TLS 1.0 using the same procedure:
Right-click on the Protocols, and select New -> Key
Type in: TLS 1.0
Right-click on TLS 1.0 key, and again select New -> Key
Type in: Server
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and leave the value to 0x00000000 (0) as we're going to disable it.
If you want to prevent the server from negotiating using TLS 1.0 to other hosts:
Right-click on TLS 1.1 key, and again select New -> Key
Type in: Client
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and leave the value to 0x00000000 (0) as we're going to disable it.
Type in: TLS 1.1
Right-click on TLS 1.1 key, and again select New -> Key
Type in: Server
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and leave the value to 0x00000000 (0) as we're going to disable it.
If you want to prevent the server from negotiating using TLS 1.1 to other hosts:
Right-click on TLS 1.1 key, and again select New -> Key
Type in: Client
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and leave the value to 0x00000000 (0) as we're going to disable it.
--
And now we're going to disable TLS 1.0 using the same procedure:
Right-click on the Protocols, and select New -> Key
Type in: TLS 1.0
Right-click on TLS 1.0 key, and again select New -> Key
Type in: Server
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and leave the value to 0x00000000 (0) as we're going to disable it.
If you want to prevent the server from negotiating using TLS 1.0 to other hosts:
Right-click on TLS 1.1 key, and again select New -> Key
Type in: Client
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and leave the value to 0x00000000 (0) as we're going to disable it.
Next, we'll need to establish this cipher suite order in group policy. Open up gpedit.msc and navigate to the following policy:
Code:
Computer Configuration\Administrative Templates\Network\SSL Configuration Settingshttps://docs.microsoft.com/en-us/windows/desktop/secauthn/tls-cipher-suites-in-windows-10-v1809
Code:
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_DHE_RSA_WITH_AES_256_GCM_SHA384,TLS_DHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA256The next step is we're going to reboot the target server, and your web server will no longer negotiate over TLS 1.1 and 1.0 since we've disabled them through the Window Registry.
I used this solution on Windows Server 2019 + IIS 10.0, but I think this solution should work on an earlier version of Windows too
If your client apps not communicating with the server after you disabled both TLS 1.1 and 1.0 it's because Windows 7 doesn't have TLS 1.2 enabled by default, so we'll need to enable it.
To enable it, we'll do similar with above, go to Windows Registry Editor (regedit.exe) and head to:
Right-click on the Protocols, and select New -> Key
Type in: TLS 1.2
Right-click on TLS 1.2 key, and again select New -> Key
Type in: Client
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and set the value to 1 as we're going to enable it.
To enable it, we'll do similar with above, go to Windows Registry Editor (regedit.exe) and head to:
Code:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Right-click on the Protocols, and select New -> Key
Type in: TLS 1.2
Right-click on TLS 1.2 key, and again select New -> Key
Type in: Client
Inside the Server key, right-click, select New -> DWORD (32-bit) Value
Type in: Enabled and set the value to 1 as we're going to enable it.
